Advancing Business Goals With Proactive Cyber Solutions
Every business is distinct and thus requires bespoke protective measures that are easy to use and proactive in nature. With our next-generation cybersecurity solutions, we mitigate threats, ensuring that your business is secure, compliant, and future-ready.
Ensuring Robust Cybersecurity with Advanced Threat Detection and Swift Response
Ensuring Robust Cybersecurity with Advanced Threat Detection and Swift Response
Cybersecurity and Data Protection Sophisticated AI Technical Solutions
Protect your business with advanced AI technologies. Our solutions utilizing AI, blockchain, and cloud technology offer reliable business-grade security while ensuring private data protection.
AI-Powered Threat Detection & Fast Response
- Computer access is monitored around-the-clock by AI which ensures any threats will be dealt with immediately.
- Security systems are trained to recognize and learn behavior patterns to identify anomalies swiftly.
- Immediate action is taken to mitigate damages. To improve analysis and decision making all data is gathered and analyzed from a single security data repository.
Trustworthy Data Masking and Encryption for Your Business
- Data is well protected with encryption whether in motion or stored.
- AI helps conceal personal information to guarantee safety and privacy.
- Meet global standards like HIPAA,GDPR,PCI-DSS.
- Multiple levels of access denial are enforced on the cloud.
Zero Trust Security, Smart Access Control
- MFA, Smart Identity Check, and Biometric ID are required for user acceptance.
- Verification techniques other than the bare minimum will be utilized.
- Access is limited strictly to what’s necessary. Nothing more is to be added.
- With every interaction, AI adapts the level of access granted based on behavior and associated risk thresholds.
- Safely and seamlessly using one sign-on (SSO) enables access to multiple resources.
Blockchain for Secure Transactions & Data Integrity
- Smart contracts eliminate the possibility of manipulation in online transactions.
- Decentralized IDs aid in the prevention of identity theft or unauthorized access.
- Blockchain aids in the easy retrieval of comprehensive tracking and audit records.
- Data is protected with cryptographic claims of integrity through data tampering.
Sectors We Empower with Technology
The tailored IT and cybersecurity services we provide are customized to solve all of your problems. We help grow your business. We make sure that from protecting critical information to creating robust systems, you can expand with peace of mind. Technology serves you regardless of whether you are in finance, healthcare, retail, or other sectors.
Finance & Banking
- Transactions are safeguarded by Encryption and Fraud Detection.
- Compliance-focused FinTech apps.
- DevOps and Cybersecurity analysts with relevant experience.
Healthcare
- Protecting data with HIPAA compliance and secure EHR systems.
- Telehealth development with strong encryption.
- Outsource health tech development and support.
E-Commerce & Retail
- Prevent fraud and secure onsite payments.
- Custom ecommerce platform development.
- ProFront and backend development services.
Education & Edtech
- Protection of digital content and student data.
- Custom LMS and mobile learning application development.
- EdTech developers and UX UI designers staffing.
Industries & Businesses That Benefit from AI/ML & Automation Development Services
The tailored IT and cybersecurity services we provide are customized to solve all of your problems. We help grow your business. We make sure that from protecting critical information to creating robust systems, you can expand with peace of mind. Technology serves you regardless of whether you are in finance, healthcare, retail, or other sectors.
Finance & Banking
- Transactions are safeguarded by Encryption and Fraud Detection.
- Compliance-focused FinTech apps.
- DevOps and Cybersecurity analysts with relevant experience.
Healthcare
- Protecting data with HIPAA compliance and secure EHR systems.
- Telehealth development with strong encryption.
- Outsource health tech development and support.
E-Commerce & Retail
- Prevent fraud and secure onsite payments.
- Custom ecommerce platform development.
- ProFront and backend development services.
Education & Edtech
- Protection of digital content and student data.
- Custom LMS and mobile learning application development.
- EdTech developers and UX UI designers staffing.
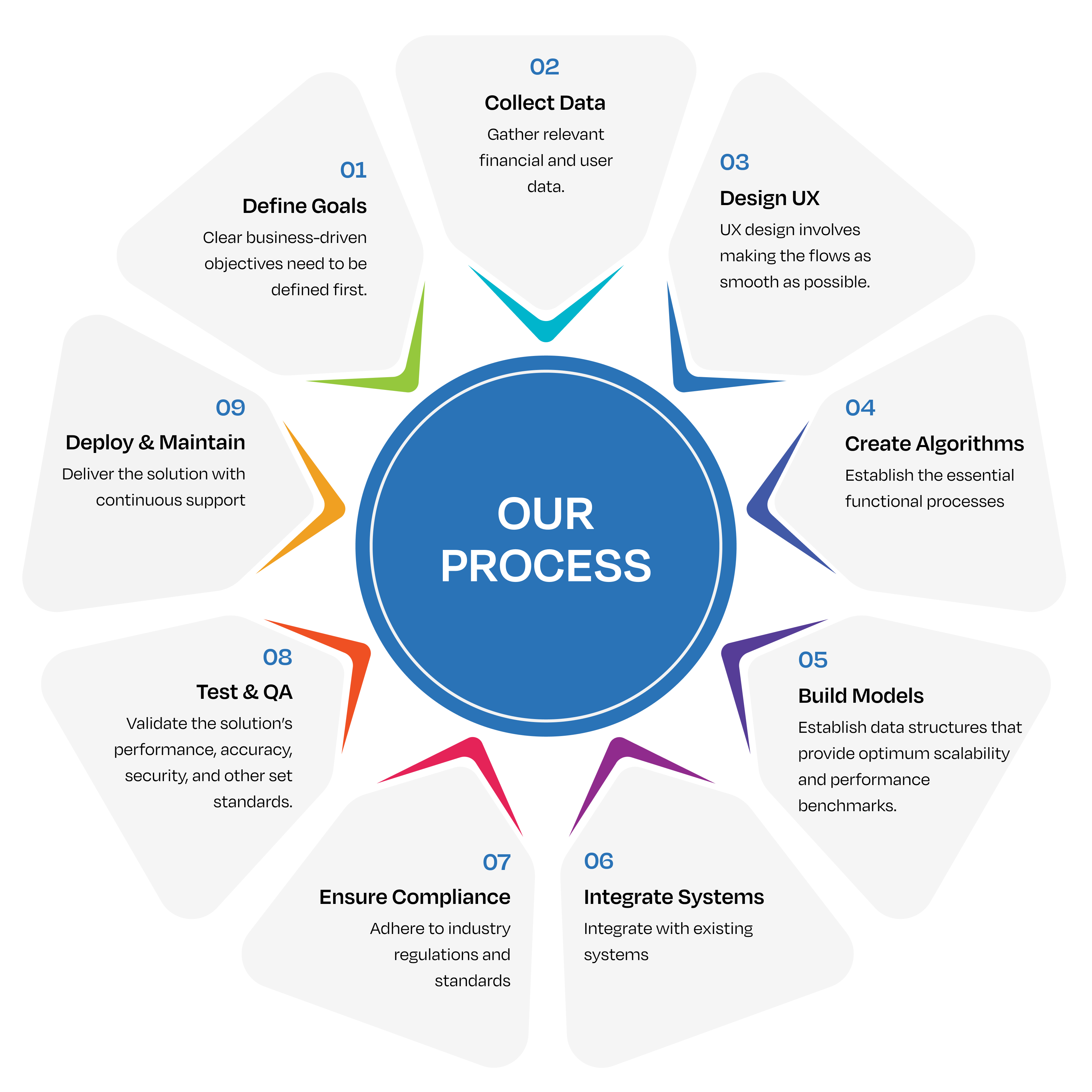
Our Proven Process for Building AI-Powered Solutions
We specialize in cloud solution development, enabling companies to migrate, optimize, and grow their digital infrastructure with high-performing, secure cloud services. Our systematic cloud development process guarantees smooth integration, compliance, and efficiency and accelerates digital transformation.
Our AI Integration Tech Stack for Cybersecurity & Data Protection
Our cybersecurity solutions are powered by cutting-edge AI and machine learning technologies, ensuring real-time threat detection, automated risk mitigation, and enhanced data protection. We integrate an advanced AI tech stack to safeguard businesses against cyber threats while optimizing security operations with intelligent automation.
Whisper
GPT 4o
PaLM 2

Claude Ai
Dalle-2
Llama-3
Gemini Ai

Vicuna
Mistral AI
Bloom-560m
Benefits of Innovative Software Solutions
Healthcare software development increases operational effectiveness, enhances patient care, and simplifies processes. From efficient data collection and automated workflow processes to AI telemedicine and diagnostics, it enables advanced, rapid, and precise healthcare solutions. Embrace modern technology and secure your medical services for the future.
Related Blogs
Schedule a 15-Minutes call
Let’s make things happen and take the first step toward success!
Got Ideas? We’ve Got The Skills.
Let’s Team Up!
Let’s Team Up!
What happens next?













